Asa 5505 No Dmz Name If
Posted : admin On 18.10.2019Lab instructions1. Configure NAT to allow LAN users to access the INTERNET2.
Configure NAT to allow DMZ servers to access the INTERNET3. Configure inbound NAT rule to allow access to the 172.16.1.10 DMZ webserver from the Internet with 148.12.56.68 public IP address.4. Configure ICMP rules to allow laptop1 to ping 148.12.56.1 internet router and any internet resource. An access-list, named OUTSIDE, will be configured to allow incoming echo-reply and unreachable ICMP replies5.Configure the required access-lists on the internet facing interface to allow incoming trafic to the DMZ webserver6.Test HTTP connectivity from the Public laptop to the DMZ webserver (Solution 1. Configure NAT to allow LAN users to access the INTERNETIn this lab, the AutoNAT feature of ASA 5506-X firewall is used to configure the NAT rules that allow the hosts on the LAN segments to connect to the Internet.
Network Address Translation is needed because these internal hosts use private IP addresses which are not routable on the Internet. Network Address Translation makes the addresses so that they look like the ASA's outside interface IP address. AutoNAT suits best if the ASA external IP changes frequently (DHCP).AutoNAT configuration for the LAN subnet is done by creating a network object representing each LAN subnet.
In the end, Cisco ASA DMZ configuration example and template are also provided. The information in this session applies to legacy Cisco ASA 5500s (i.e. ASA 5505, 5510 and 5520) as well as the next-gen ASA 5500-X series firewall appliances. Since ASA code version 8.3, there was a major change introduced into the NAT functionality by Cisco. Cisco ASA5505 DMZ setup with ASDM. ASA Version 8.2(5)! Hostname ciscoasa enable password 6ZoFBEConbp3Z7DJ encrypted passwd 2KFQnbNIdI.2KYOU encrypted names name XO-Gateway name 10.23.141.93 SEO1-IN name SEO1-OUT name 10.23.141.62 SEO2-IN name SEO2-OUT name 10.23.141.94 SEO3-IN.
In each of these objects, a dynamic nat rule is configured to conduct Port Address Translation (PAT) on these clients as they pass from the inside to the outside interface.The name of each interface, configured with nameif, is used in the AutoNAT command: nat (inside,outside) dynamic interface object network LANsubnet 192.168.20.0 255.255.255.0nat (inside,outside) dynamic interface2. Configure NAT to allow DMZ servers to access the INTERNETThe same configuration as for the LAN subnet is done for the DMZ servers subnet. The source interface name is replaced by the DMZ named interface. Object network DMZsubnet 172.16.1.0 255.255.255.0nat (DMZ,outside) dynamic interface3. Configure inbound NAT rule for 172.16.1.10 DMZ webserver accessThe following NAT rule statically maps the DMZ 172.16.1.10 webserver address to the 148.12.56.68 external address. Rule is bi-directional.
Object network webserverhost 172.16.1.10nat (DMZ,outside) static 148.12.56.684. Configure ICMP rulesConfigure an extended access-list with the required rules to accept incoming echo replies. Access-list OUTSIDE extended permit icmp any any echo-replyaccess-list OUTSIDE extended permit icmp any any unreachable5.Configure the required ACL to allow incoming trafic to the DMZ webserverComplete the previous access-list with the rules to allow inbound HTTP trafic and apply the ACL to the outside interface. Object network webserver-external-iphost 148.12.56.68access-list OUTSIDE extended permit tcp any object webserver eq wwwaccess-list OUTSIDE extended permit tcp any host 148.12.56.68 eq wwwaccess-group ICMP-REPLY in interface outside6.Test HTTP connectivity Internet to the DMZ webserverOpen a web browser on the 'Public LAPTOP' located on the right of the network diagram.The connection to should display the following welcome page.ASA 5505 and 5506-X comparison ASA 5506-X - Layer 3 interfacesThe new ASA 5506-X firewall provided in Packet Tracer 7.2 is configured with 8 layer 3 network interfaces.
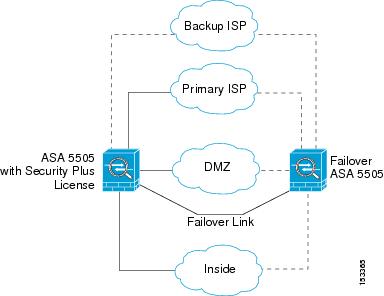
I have an ASA 5505 with the security plus package and would like to setup a DMZ for an ISA server and a web server. Right now I have been able to setup a vlan for the dmz, was able to setup an external ip address for one of the dmz servers, and able to get out to the internet on both dmz servers. The problem I'm having is pinging either dmz servers from the inside network and pinging the inside from the dmz network. Of course I am also not able to connect to any of the websites on the web server from the inside. Your help would be greatly appreciated.
Cisco Asa 5505 Basic Configuration
X=outside ip address. Put in these commands:no access-group insideaccessout out interface inside. I just found out that I now am able to ping the inside from the dmz but cannot ping the dmz from the inside.